We at FS Impact Finance communicate and interact with our partners and clients all over the world, increasingly relying on information systems, electronic networks, the cyberspace.
We benefit from the digital age, nevertheless organisations such as ours must step up our cyber governance and security apparatuses to fight vulnerabilities to ever-increasing scale and impact of cybercrimes, phishing emails to “CEO-Fraud”.
The world isn’t run by weapons anymore, or energy, or money. It’s run by ones and zeros – little bits of date – it’s all electrons… There’s a war out there, a world war. It’s not about who has the most bullets. It’s about who controls the information – what we see and hear, how we work, what we think. It’s all about information.
Lines from the character ‘Cosmos’, in the movie Sneakers, MCA/Universal Pictures, 1992. Source: European Crime Prevention Network/Cybercrime: A theoretical overview of the growing digital threat EUCPN Secretariat, February 2016, Brussels
With the COVID-19 pandemic we as individuals and as a company are even more vulnerable to cybercrime due to the impact of social distancing. Communication via computer systems, mobile devices and the Internet is the norm.
On 27th March 2020, the Council of Europe’s Cybercrime Division issued an interesting guidance paper to raise alertness and reinforce security measures. They cite the following examples that malicious actors are exploiting:
- Phishing campaigns and malware distribution through seemingly genuine websites or documents providing information or advice on COVID-19 are used to infect computers and extract user credentials.
- Ransomware shutting down medical, scientific or other health-related facilities where individuals are tested for COVID-19 or where vaccines are being developed in order to extort ransom.
- Attacks against critical infrastructures or international organisations, such as the World Health Organization.
- Ransomware targeting the mobile phones of individuals using apps that claim to provide genuine information on COVID-19 in order to extract payments.
- Offenders obtaining access to company systems by targeting employees who are teleworking.
- Fraud schemes where people are tricked into purchasing goods such as masks, hand sanitizers, but also fake medicine claiming to prevent or cure SARS-CoV-2.
- Misinformation or fake news are spread by trolls and fake media accounts to create panic, social instability and distrust in governments or in measures taken by their health authorities
We all must be extra-cautious and reinforce security measures. Here is some information provided by Europol on how to make your home a cyber safe stronghold (information available in several languages), along with safe teleworking tips and advice:
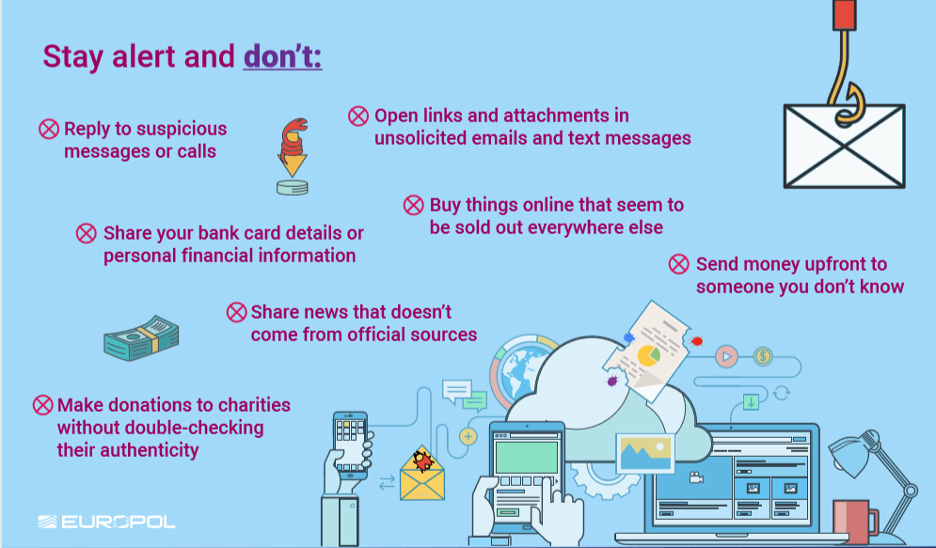
With the increasing number of people working remotely and interconnected with their office, “cyber hygiene” is key. The EU Agency for Cybersecurity issued (24th March 2020) the following recommendations for teleworking:
1. Recommendations for employers and staff
The following recommendations for maintaining an adequate level of cybersecurity when teleworking are divided into those for employers and for staff.
Recommendations for employers
- Ensure that the corporate VPN solution scales and is able to sustain a large number of simultaneous connections.
- Provide secure video conferencing for corporate clients (both audio/video capabilities).
- All the corporate business applications must be accessible only via encrypted communication channels (SSL VPN, IPSec VPN).
- Access to application portals should be safeguarded using multifactor authentication mechanisms.
- Prevent the direct Internet exposure of remote system access interfaces (e.g. RDP).
- Mutual authentication is preferred when accessing corporate systems (e.g. client to server and server to client).
- Provide, where possible, corporate computers/devices to teleworking staff; ensure that these computers/devices have up-to-date security software and security patch levels and that users are regularly reminded to check patch levels. It is advisable that a replacement scheme for failing devices is also in place.
- BYOD (Bring your own device) such as personal laptops or mobile devices must be vetted from the security standpoint using NAC, NAP platforms. (e.g. patch check, configuration check, AV check, etc.).
- Ensure that adequate IT resources are in place to support staff in case of technical issues while teleworking; provide relevant information, e.g. on contact points, to staff.
- Ensure policies for responding to security incidents and personal data breaches are in place and that staff is appropriately informed of them.
- Ensure that any processing of staff data by the employer in the context of teleworking (e.g. time keeping) is in compliance with the EU legal framework on data protection.
Recommendations for staff on teleworking
- Use corporate (rather than personal) computers where possible – unless BYOD has been vetted as per relevant point under Section 1 above. As far as possible, do not mix work and leisure activities on the same device and be particularly careful with any emails referencing the corona virus.
- Connect to the internet via secure networks; avoid open/free networks. Most wifi systems at home these days are correctly secured, but some older installations might not be. With an insecure connection, people in the near vicinity can snoop your traffic (more technical people might be able to hijack the connection). That having been said, the risk is not that much higher than when using public ‘open networks’ except for the fact that presumably people will be in the same place for a long time. The solution is to activate the encryption if it hasn’t been done already and/or to adopt a recent implementation. Note that this risk is somewhat mitigated by using a secure connection to the office.
- Avoid the exchange of sensitive corporate information (e.g. via email) through possibly insecure connections.
- As far as possible use corporate Intranet resources to share working files. On the one hand, this ensures that working files are up-to-date and at the same time, sharing of sensitive information across local devices is avoided.
- Be particularly careful with any emails referencing the corona virus, as these may be phishing attempts or scams (see below). In case of doubt regarding the legitimacy of an email, contact the institution’s security officer.
- Data at rest, e.g. local drives, should be encrypted (this will protect against theft / loss of the device).
- Antivirus / Antimalware must be installed and be fully updated.
- The system (operating system and applications used, as well as anti-virus system) needs to be up to date.
- Lock your screen if you work in a shared space (you should really avoid co-working or shared spaces at this moment. Remember, social distancing is extremely important to slow down the spread of the virus).
- Do not share the virtual meeting URLs on social media or other public channels. (Unauthorized 3rd parties could access private meetings in this way)
2. Phishing scams linked to COVID-19
It is important to step up awareness of digital security during this time as we have already seen an increase in phishing attacks. Attackers are exploiting the situation, so look out for phishing emails and scams.
In the current situation, one should be suspicious of any emails asking to check or renew your credentials even if it seems to come from a trusted source. Please try to verify the authenticity of the request through other means, do not click on suspicious links or open any suspicious attachments.
- Be very suspicious of emails from people you don’t know- especially if they ask to connect to links or open files (if in doubt phone your security officer).
- Emails that create an image of urgency or severe consequences are key candidates for phishing – in these cases always verify via an external channel before complying.
- Mails sent from people you know, but asking for unusual things, are also suspect – verify by phone if possible.
There is more useful information and guidance available in the internet, please also check out the public awareness and prevention guides published by EUROPOL.
Happy reading, enhancing the security culture and transformation of individual steps into operational tools and best practices in your organisation!













